Photo: screenshot
Mobile applications are not exempted from implementing this effective method, as some applications are changed in their code to harm the users
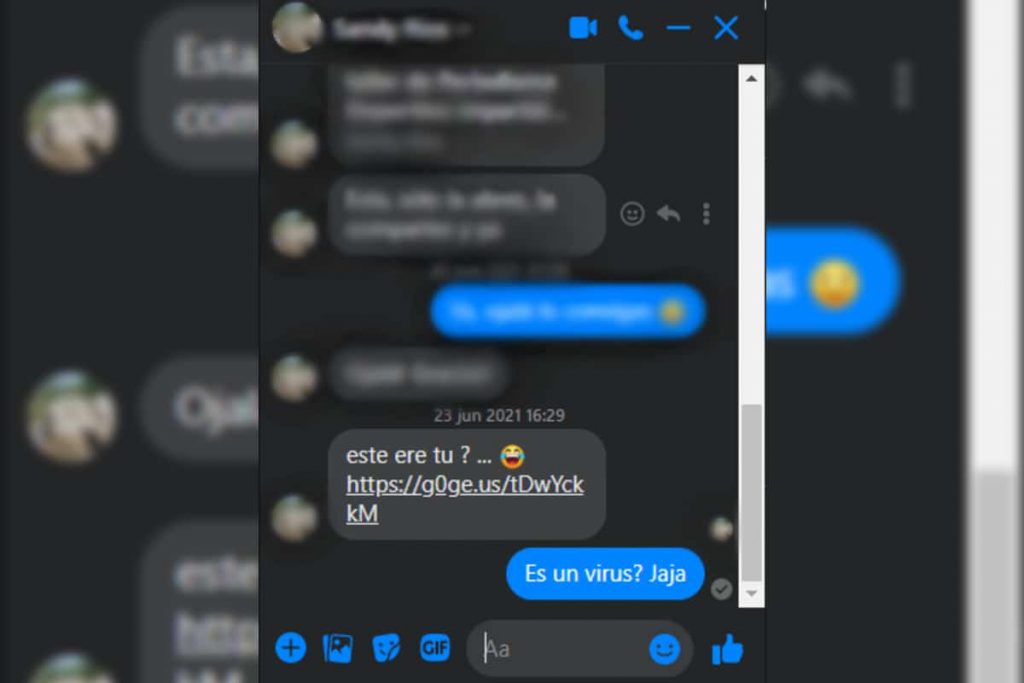
For a long time there was a message from a friend or contact you added Facebook social networking site And he asked:Are you the one in the video?“.even though a series of popups appear at the time of accessing the link.
This is part of the strategy of a group with malicious intent intending to gain access to sensitive data, such as Picturesor audio files or documents stored within servers messenger.
The technique in particular is called phishing It is considered the “crime of deceiving people into sharing confidential information such as passwords and credit card numbers.”
According to the gate MalwareAs in hunting, there is more than one way to catch the victim, but there is a tactic phishing which is the most common, which we put at the beginning; Impersonate the victim by trying to link them to a malicious link.
When we get to a pop-up, the command may take us to a known site, such as a portal to open our email, a social network or even a banking portal.
Keep in mind that cybercriminals can use tools to simulate these fake windows, so we must pay special attention to the security elements of our browser.
An example of a secure site is the padlock that appears next to the URL, link, or link we’re visiting. This means that the site has been verified by a regulator and is the organization or company it belongs to.
In addition, this element ensures that the information we enter on this page is transmitted over the Internet in an encrypted form, and therefore cannot be read by anyone who can intercept it.
They can still catch you
Despite knowing these security elements, viruses can give you a hard time if you let them. Technique phishing It aims to scare you into providing the data they are looking for.
This technology is one of the oldest technologies on the Internet and it has spread on popular sites like old Messenger and emails, now they are traveling through social networks, they have adapted to new technologies.
It is always important to be suspicious of messages being sent to us with suspicious links, which almost always do not end in .com or are unreadable towards a popular site, even if they are sent to us by people we trust.
water with apps
Mobile applications are not exempt from implementing this effective method, as some applications are changed in their code to harm the users.
It almost always happens when third-party tools are installed, that is, they are not in the Google Play Store or the like in IOS devices, because when they have modifications, they cannot be registered in the application libraries of these two companies.
However, that doesn’t mean it doesn’t, since there are records that some apps released malware from apps in the PlayStore, as happened with FlixOnline, a fraudulent service that claims to allow users to watch Netflix content from around the world on their sites. mobile phones.
These modded apps create windows that simulate logging into a social network, banking app, or the like. Just like the PC version.
CT

“Problem solver. Proud twitter specialist. Travel aficionado. Introvert. Coffee trailblazer. Professional zombie ninja. Extreme gamer.”


More Stories
Below is the schedule of pension payments as of July 2022. Find out what benefits you will get after the changes [17.07.2022]
Overview of the new electric sports cars for the Hyundai Ioniq 5 N and Ioniq 6 N
Portugal has launched a floating solar power plant. It is the largest structure of this type in Europe – Economy